- The percentage of spam in email traffic was up 2.2 percentage points from March and averaged 77.2%.
- The percentage of phishing emails remained unchanged from March and amounted to 0.01%.
- In April, malicious files were found in 2.8% of all emails — the same amount as in the previous month.
- Over 20% of phishing attacks in April targeted Facebook users.
New tricks spotted in fraudulent and malicious spam
Spammers who spread malicious code and phishing emails are still looking for the best shortcut to reach computer users. Malicious spam is developing quickly, and malicious users are systemically adding to their arsenal of tricks, both with technical innovations and with new tactics involving social engineering.
Wikipedia and Amazon — bad experience?
In April, we detected spam that at first glance looked just like your typical malicious mass mailing designed to look like an official Facebook notification. The email, allegedly from the social network, announced a new Friend Request on Facebook. Like most of the emails made to look like Facebook notifications over the past year, this mailing was well done and looked like the real thing, at first glance. According to the plans of the malicious users, if the user clicked on any of the links in the email, he would be taken to a website infected with malicious code, rather than Facebook. Sounds familiar, doesn’t it? There is just one difference here — the links in the emails didn’t take users to hacked domains or to sites registered in the .in or co.cc domains, but to pages on Wikipedia and Amazon.

Apparently, malicious users seeded malicious script on their newly created Wikipedia pages as well as on pages made to look like advertisements for pre-owned goods on Amazon.com. Why “apparently”? Because this tactic was not the most effective, as the teams on both services responded promptly, and by the time the links were spread, the pages were already disabled.
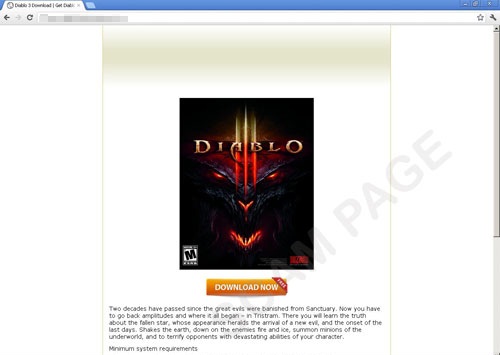
Diablo III – pre-release phishing
In early June, the long-awaited game Diablo III is expected to hit the shelves. IT security professionals have some concerns associated with this particular game, and Blizzard has officially permitted the trade of in-game items in this new MMORPG. It is reasonable to expect that phishers will quickly set their sights on Diablo III players. But no one expected malicious users to start using this game even before it was released.
Phishing emails appeared in spam traffic playing off of the impatience of gamers anxiously awaiting Diablo III’s release. The emails stated that they would be given the opportunity to play a beta version of Diablo III for a specific period of time. In order to do so, they would need to enter their battle.net account information (a resource where Blizzard account information is stored). Of course, the link in the email did not lead to the specified site, but to a phishing webpage. Each email was slightly different, but the basic features were ultimately the same.

After obtaining the registration data from a battle.net user, malicious users would then have access to that user’s accounts for popular games like World of Warcraft and Starcraft, which are still in high demand on the black market.
Political spam
Political spam got back in action in April, primarily targeting US and French readers. Mentions of Barack Obama in spam emails were as frequent as they were during the first year after his election. Furthermore, his name is used not only in political emails “exposing his political course” or pointing to the allegation that the President of the US “is afraid of losing the upcoming election,” but also in emails advertising a variety of traditional spammer products. For example, his name is mentioned in one mass spam mailing offering Viagra.

With the upcoming elections in the US, Internet user interest in the battle for the presidency and the personalities of the candidates and the current president will only grow. Spammers will doubtless fan the flames of this interest by spreading propaganda, in addition to continuing to take advantage of this interest for their own purposes. In the months to come, we expect an increase in the number of emails with links allegedly leading to web pages with scandalous information about the candidates and the elections in general. Furthermore, the links will likely take users to advertisements for libido-boosting medications in the best case scenario (as in the example above), or to a malicious program in the worst case scenario.
French political spam is also more active these days, although we did expect a larger volume of political spam mailings in France during the frenzy of the recent presidential race there. The spam emails that we detected were few in number. They included advertisements for T-shirts with pro-Sarkozy slogans.

Other hot topics
The complex situation in Syria has also become the subject of spam emails. “Nigerian” spammers are actively mailing out messages from “lawyers and bank clerks working in the country.” At month’s end, we had also detected emails from “Assad’s wife.” We regularly encounter emails from the “family members of leaders” of a variety of countries facing unstable conditions. Sometimes Nigerian spam emails are even presented as having been written by these very leaders. So it is altogether possible that in the future we will see emails allegedly written by Bashar al-Assad himself. The Assads’ children are still quite young, so we are unlikely to see any of these emails allegedly written by them, although you never know. After all, nothing is sacred to spammers, and a crisis in any country is nothing more than an opportunity to rake in some cash.
We are also seeing a surge in the amount of spam exploiting the European football championship. This event is due to start in June, and Internet users are increasingly interested from day to day. Many spam mailings offer rooms to football fans that haven’t yet made hotel reservations in Poland and Ukraine. However, the accommodation offered by the spammers is bare-bones at best, while the prices have been greatly inflated.
The Summer Olympics in London are currently the focus of attention among “lottery” scammers. Just about every week we see emails announcing lottery winnings, allegedly from a lottery held by the Olympics Foundation.

Statistical summary
Sources of spam

Sources of spam in April 2012 (TOP 20)
In April, the Top 20 sources of spam underwent some major changes from prior months.
The most noticeable change over the month was the US jumping from 20th to 2nd place in the rankings. The proportion of spam originating in the US surged by over 7 percentage points. The amount of spam coming from China also increased – by 5 percentage points – and that country is now ranked 5th among the world’s top sources of spam. Meanwhile, the percentage of unwanted correspondence originating in Indonesia fell by 5.2 percentage points. This Asian country fell 10 places and ended up in 12th place last month.
We presume that this change in the spam landscape correlates with the redistribution of powerful spammer-run botnets and their relocation from regions where spam operations have been low-level over the past year. Note that both the US and China (and Hong Kong in particular) were some of the top targets in the first quarter of 2012 for spammers spreading malicious mailings. The infection of new computers in these countries has clearly led to the growth of new botnets.
The other changes in the ratings among sources of spam were limited to no more than 2.5 percentage points.
Malware in mail traffic
In April, malware was found in 2.8% of all emails, which more or less matches the levels detected in March’s mail traffic.
The distribution of email antivirus detections by country

The distribution of email antivirus detections by country, April 2012
Just as it was in the first quarter of 2012, the US has taken the leading position in terms of the number of email antivirus detections. The percentage of Kaspersky Mail Antivirus detections in the US rose only slightly, by just 0.64 percentage points.
Australia (-3.9 percentage points) and Hong Kong (-2 percentage points), countries that had been ranked second and third, respectively, in March, conceded their places to Vietnam in April, which climbed up from 4th to 2nd place. The proportion of mail antivirus detections in Vietnam increased by 2.4 percentage points.
The percentages of detections in other countries fluctuated within a range of 2 percentage points.
Top 10 malicious programs spread by email

Top 10 malicious programs spread via email in April 2012
Some 13.7% of all Kaspersky Mail Antivirus detections are for the traditional leader in our Top 10: Trojan-Spy.HTML.Fraud.gen. Detections of this Trojan were 1.6 percentage points higher in April than in March. This malicious program is designed to look like an HTML page serving as a registration form for a financial organization or an online service. The registration data entered on the page are then sent to malicious users.
The usual suspects in our Top 10 — the email worms Email-Worm.Win32.Bagle.gt, Email-Worm.Win32.Mydoom.m and Email-Worm.Win32.NetSky.q — are in third, fifth, and ninth place in this month’s ranking respectively. Readers may recall that the functions of the Mydoom and Netsky families of worms are limited to the harvesting of email addresses from infected computers, and sending themselves to these addresses. Bagle.gt is the only worm in the Top 10 that is also capable of sending requests to online resources and then downloading malicious programs.
We should draw attention to the appearance of the script Trojan — Trojan-Downloader.JS.Iframe.cvq — in April’s Top 10. It accounted for nearly 2% of all mail antivirus detections. Another 10% or so of all mail antivirus detections in April were represented by script-based malicious programs that were detected using proactive methods. This is relatively worrisome, as script-based threats in HTML emails launch destructive actions as soon as a recipient opens the email.
Phishing
The percentage of phishing emails remained unchanged from March and amounted to 0.01%.

The distribution of the Top 100 organizations targeted by phishers, by category — April 2012
This rating is based on our anti-phishing component detections activated every time a user attempts to click on a phishing link, regardless of whether the link is in a spam email or on a web page.
In April, we saw a major change in the top phisher-targeted organizations: for the first time in four months, financial organizations (23.61%) left first place, and were replaced by social networking sites (28.8%). The percentage of social networking sites targeted in phishing attacks increased by almost 6 percentage points. The main contributing factor to that rise was due to the numerous attacks on Facebook: over 20% of all phishing attacks in April targeted Facebook users.
Compared to March, the percentage of attacks against financial organizations fell somewhat, as did the percentage of attacks against online stores and search engines, IT vendors and organizations in the “other” category. All of these changes were within a range of 1.5 percentage points.
As a result, one can see a slight change in the focus of phishing attacks increasingly toward the users of social networks.
Spam by category

Spam by category in April 2012
The percentage of the traditional leaders in the top spam categories — Computer Fraud and Personal Finances — changed only slightly in April. The former fell by 2.2 percentage points, and the latter rose by 0.8 percentage points.
The share of advertisements for online casinos remains high at just over 6%.
Most spam emails advertising online casinos clearly show signs of fraud, malicious code, or something else. The Personal Finances category is more often than not made up of dubious offers for cheap loans or fast cash, and there is usually something fishy about them.
Having reviewed these data, one can confidently say that more than half of all spam in April aimed to steal financial or personal information from computer users, as well as indirectly steal their money and install malicious code on their computers.
Incidentally, the most substantial change that we noted from March to April was a rise of 4.75 percentage points in the Interior Design spam category. In April, Kaspersky Lab noted several mass mailings in this category. Apparently, this surge in interior design-themed spam is connected to the “spring cleaning” advertising campaigns pushed by many furniture and renovation companies.
The percentages of other spam categories fluctuated only slightly in April, within a range of 1.5 percentage points.
Conclusion
It needs to be said that spam is posing more of a threat than ever: there is a high percentage of malicious code in attachments, and Kaspersky Lab is detecting a considerable number of spam emails containing malicious links. Furthermore, IT security professionals are seeing even more spam containing script-based threats, which means that even just opening an email could put users at risk. The fact that these mailings continue to spread from month to month demonstrates that Internet users are not sufficiently informed; spam would not be such an attractive means of proliferating malicious code if it were not so lucrative for cybercriminals. Internet users often do not even suspect that their computer’s performance faces any threat at all, not to mention their personal data or cash, when they open a spam email.
In the months to come, we expect a return of the all-too-familiar spam mailings with scandalous news items about current US President Barack Obama. Furthermore, phishing attacks will likely focus more on social networking sites, and possibly online games — as summer vacation is upon us, students on break from school will be more active online. While these users tend not to have bank accounts, they do spend a lot of time on social networks and other online entertainment.
securelist.com